[Информационная безопасность] Enrolling and using Token2 USB Security keys with UserLock MFA
Автор
Сообщение
news_bot ®
Стаж: 7 лет 9 месяцев
Сообщений: 27286
UserLock is a user login security system for on-premises Windows Active Directory designed by ISDecisions. It works alongside Active Directory to protect access to Windows systems. With specific and customizable user login rules and real-time monitoring, UserLock reduces the risk of external attacks and internal security breaches while helping to address regulatory compliance. UserLock is one of the few solutions existing on the market that allows implementing multi-factor authentication for logging on to Windows computers with Active Directory domain membership or standalone terminal servers.
Previous versions of UserLock are allowing using Token2 programmable tokens as the second factor (TOTP protocol). Starting from version 11, UserLock natively supports Token2 T2F2 Security keys (second-generation only: ALU, AZ, NFC and Bio) by utilizing the HOTP functionality of these keys. In this article, we will show the procedures required to enrol and use Token2 security keys to log in to your Windows workstation protected with UserLock.1. Enable MFA for a userthis step is done by the administrator of the systemIn the UserLock management console, navigate to "Protected Accounts" and click on "Protect a new account" button. 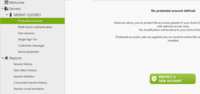
Then follow the wizard's instruction to protect a single account or a group. The steps below show enabling UserLock protection for "mfauser" local account on a standalone server as an example.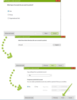
Then, double-click on the newly created protected account record to open its properties window.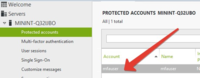
Scroll down to Multi-factor authentication section and configure settings for this user. On the screenshot below, we configured the user with the most strict settings: MFA is enabled for both workstation and server logins, and the second factor will be asked on every logon.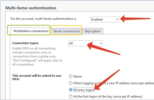
Click Apply/OK to finish this step. Now, the next time this user logs in, a wizard asking to configure the second factor will appear and the login will only be possible after this process is completed successfully.2. Configuring the second factor for the userthis step is done by the userAfter the user account's UserLock protection is enabled and MFA is activated, on the next logon attempt, UserLock will prompt the user to enrol one of the second factors. We will show the process of configuring a Token2 security key as the second factor.
Choose USB token from the first window - make sure your Token2 key is plugged into a USB port before continuing.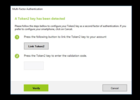
If a compatible Token2 key is detected, the system will show a "Link Token2" button to start the process.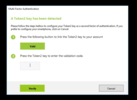
After successfully linking the security key, the button will transform to "Valid" message.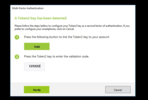
After this, set the cursor to the text field and press the button on the security key. There is no need to click "Verify" button as the key will send "Enter" keystroke to minimize user actions.
Upon successful enrollment, UserLock will prompt to enrol an additional factor for MFA (this can be a TOTP programmable token or an app, you cannot add a second USB Security key)
3. Logging in using a Token2 Security keyOnce enrollment is complete, the MFA prompt will ask to enter the OTP. 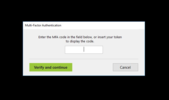
With USB security keys, users will only need to plug in the Token2 key to a USB port and press the physical button on the key . There is no additional action needed as the OTP will be sent together with "Enter" keystroke, which will submit the OTP automatically.
Frequently asked questions1. Can I use this method for Remote Desktop logins?Short answer: you can log in, but you cannot enrol.
Currently, the UserLock MFA enrollment wizard requires the security key to be plugged directly to the same machine in order to successfully complete the enrollment. Therefore, enrolling a Token2 Security Key over remote desktop is not possible. You will get an error as shown below: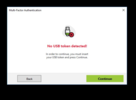
However, if the security key has already been linked to a UserLock protected account, subsequent logins are possible over RDP.2. What is the difference between using Token2 TOTP programmable tokens and Token2 Security keys with UserLock MFA?
The main difference from the user experience point of view is that with the Token2 Security keys, users do not need to manually type in the one-time password (6 digits) as with TOTP (apps or tokens). Instead, to provide the second factor to complete the login process, the user will only have to plug in the device to a USB port and press the button. The only exception to this is when using our USB programmable tokens - they can also send the code over USB by leveraging the HID/Keyboard emulation feature. Another aspect is the provisioning and login process differences, briefly shown in the comparative table below:TOTP TokensSecurity keysProvisioning requirementsAn additional device is needed(for NFC models only, USB-programmable tokens do not need any additional devices)No additional device neededProvisioning security levelMedium
Secret key transferred to end-userHigh
Provisioning done by UserLock directly on the deviceProvisioning over RDPPossibleNot possibleLogon over RDPPossiblePossible3. Can I enrol more than one USB Security key?
No, currently UserLock only allows one security key to be associated per account. You can have a TOTP (token or app) as the alternative or backup factor.4. Can I use the Token2 Security key for other services?UserLock is using the HOTP functionality of our security keys and there is only one slot available for HOTP (this is due to HID feature as the password generated by HOTP is being sent by pressing the button on the device). However, as our security keys are FIDO2 compliant (and some models FIDO2 certified), you can use them on any FIDO2-compatible resources. These keys also feature TOTP generation via a companion app.Important! It is possible to configure HOTP parameters of our security keys using our companion app - please note that doing so will break its UserLock functionality.5. Which security keys are compatible with UserLock HOTP functionality?Currently, the following models are supported:
- T2F2-ALU
- T2F2-AZ
- T2F2-NFC
- T2F2-Bio
Here is the link for a comparative table of these models. Also, it is worth mentioning the following aspects:
- If you use a system with AZERTY keyboard configured, you will have to keep "Shift" key pressed when pressing the button on the security keys. Our newer models (T2F2-AZ and T2F2-Bio) can be configured to use numeric keyboard instead, in such case, NumLock state should be on
- With T2F2-Bio the fingerprint protection does not apply to HOTP functionality. With UserLock, the fingerprint sensor will be used as a simple touch sensor to send the OTP digits (press the sensor for 2-3 seconds to send the digits).
===========
Источник:
habr.com
===========
Похожие новости:
- [Информационная безопасность, Разработка под iOS, Монетизация мобильных приложений, Контекстная реклама] Google начала обновлять iOS-приложения в соответствии с требованиями Apple
- [Информационная безопасность, Ruby on Rails, CTF] HackTheBox. Прохождение Jewel. RCE в Ruby on Rails, sudo и google authenticator, выполнение кода в gem
- [Информационная безопасность, Администрирование доменных имен, Законодательство в IT] ИБ-компании пожаловались на захват Facebook доменов для фишинг-тестов
- [Информационная безопасность, Системное администрирование, IT-инфраструктура, IT-компании] Яндекс рассказал о компрометации 4887 почтовых ящиков по вине сисадмина с высоким уровнем доступа
- [Информационная безопасность, Разработка веб-сайтов, PHP, Антивирусная защита] Невидимые символы, скрывающие веб-шелл в зловредном коде на PHP (перевод)
- [Информационная безопасность] ТОП-3 ИБ-событий недели по версии Jet CSIRT
- [Информационная безопасность, Социальные сети и сообщества] Instagram вводит вечные баны за оскорбительное поведение
- [Информационная безопасность, Криптография, Хранение данных] Пароль как крестраж: ещё один способ защитить свои учётные данные (перевод)
- [Информационная безопасность] В «Шереметьево» и «Домодедово» будут распознавать лица пассажиров вместо проверки паспорта
- [Информационная безопасность, Разработка игр, Игры и игровые приставки, IT-компании] Украденные данные CD Projekt Red проданы вне рамок аукциона
Теги для поиска: #_informatsionnaja_bezopasnost (Информационная безопасность), #_hotp, #_totp, #_active_directory, #_blog_kompanii_token2.com (
Блог компании Token2.com
), #_informatsionnaja_bezopasnost (
Информационная безопасность
)
Вы не можете начинать темы
Вы не можете отвечать на сообщения
Вы не можете редактировать свои сообщения
Вы не можете удалять свои сообщения
Вы не можете голосовать в опросах
Вы не можете прикреплять файлы к сообщениям
Вы не можете скачивать файлы
Текущее время: 29-Ноя 21:31
Часовой пояс: UTC + 5
| Автор | Сообщение |
|---|---|
|
news_bot ®
Стаж: 7 лет 9 месяцев |
|
|
UserLock is a user login security system for on-premises Windows Active Directory designed by ISDecisions. It works alongside Active Directory to protect access to Windows systems. With specific and customizable user login rules and real-time monitoring, UserLock reduces the risk of external attacks and internal security breaches while helping to address regulatory compliance. UserLock is one of the few solutions existing on the market that allows implementing multi-factor authentication for logging on to Windows computers with Active Directory domain membership or standalone terminal servers. Previous versions of UserLock are allowing using Token2 programmable tokens as the second factor (TOTP protocol). Starting from version 11, UserLock natively supports Token2 T2F2 Security keys (second-generation only: ALU, AZ, NFC and Bio) by utilizing the HOTP functionality of these keys. In this article, we will show the procedures required to enrol and use Token2 security keys to log in to your Windows workstation protected with UserLock.1. Enable MFA for a userthis step is done by the administrator of the systemIn the UserLock management console, navigate to "Protected Accounts" and click on "Protect a new account" button.  Then follow the wizard's instruction to protect a single account or a group. The steps below show enabling UserLock protection for "mfauser" local account on a standalone server as an example.  Then, double-click on the newly created protected account record to open its properties window.  Scroll down to Multi-factor authentication section and configure settings for this user. On the screenshot below, we configured the user with the most strict settings: MFA is enabled for both workstation and server logins, and the second factor will be asked on every logon.  Click Apply/OK to finish this step. Now, the next time this user logs in, a wizard asking to configure the second factor will appear and the login will only be possible after this process is completed successfully.2. Configuring the second factor for the userthis step is done by the userAfter the user account's UserLock protection is enabled and MFA is activated, on the next logon attempt, UserLock will prompt the user to enrol one of the second factors. We will show the process of configuring a Token2 security key as the second factor.  Choose USB token from the first window - make sure your Token2 key is plugged into a USB port before continuing.  If a compatible Token2 key is detected, the system will show a "Link Token2" button to start the process.  After successfully linking the security key, the button will transform to "Valid" message.  After this, set the cursor to the text field and press the button on the security key. There is no need to click "Verify" button as the key will send "Enter" keystroke to minimize user actions.  Upon successful enrollment, UserLock will prompt to enrol an additional factor for MFA (this can be a TOTP programmable token or an app, you cannot add a second USB Security key)  3. Logging in using a Token2 Security keyOnce enrollment is complete, the MFA prompt will ask to enter the OTP.  With USB security keys, users will only need to plug in the Token2 key to a USB port and press the physical button on the key . There is no additional action needed as the OTP will be sent together with "Enter" keystroke, which will submit the OTP automatically. Frequently asked questions1. Can I use this method for Remote Desktop logins?Short answer: you can log in, but you cannot enrol. Currently, the UserLock MFA enrollment wizard requires the security key to be plugged directly to the same machine in order to successfully complete the enrollment. Therefore, enrolling a Token2 Security Key over remote desktop is not possible. You will get an error as shown below:  However, if the security key has already been linked to a UserLock protected account, subsequent logins are possible over RDP.2. What is the difference between using Token2 TOTP programmable tokens and Token2 Security keys with UserLock MFA? The main difference from the user experience point of view is that with the Token2 Security keys, users do not need to manually type in the one-time password (6 digits) as with TOTP (apps or tokens). Instead, to provide the second factor to complete the login process, the user will only have to plug in the device to a USB port and press the button. The only exception to this is when using our USB programmable tokens - they can also send the code over USB by leveraging the HID/Keyboard emulation feature. Another aspect is the provisioning and login process differences, briefly shown in the comparative table below:TOTP TokensSecurity keysProvisioning requirementsAn additional device is needed(for NFC models only, USB-programmable tokens do not need any additional devices)No additional device neededProvisioning security levelMedium Secret key transferred to end-userHigh Provisioning done by UserLock directly on the deviceProvisioning over RDPPossibleNot possibleLogon over RDPPossiblePossible3. Can I enrol more than one USB Security key? No, currently UserLock only allows one security key to be associated per account. You can have a TOTP (token or app) as the alternative or backup factor.4. Can I use the Token2 Security key for other services?UserLock is using the HOTP functionality of our security keys and there is only one slot available for HOTP (this is due to HID feature as the password generated by HOTP is being sent by pressing the button on the device). However, as our security keys are FIDO2 compliant (and some models FIDO2 certified), you can use them on any FIDO2-compatible resources. These keys also feature TOTP generation via a companion app.Important! It is possible to configure HOTP parameters of our security keys using our companion app - please note that doing so will break its UserLock functionality.5. Which security keys are compatible with UserLock HOTP functionality?Currently, the following models are supported:
=========== Источник: habr.com =========== Похожие новости:
Блог компании Token2.com ), #_informatsionnaja_bezopasnost ( Информационная безопасность ) |
|
Вы не можете начинать темы
Вы не можете отвечать на сообщения
Вы не можете редактировать свои сообщения
Вы не можете удалять свои сообщения
Вы не можете голосовать в опросах
Вы не можете прикреплять файлы к сообщениям
Вы не можете скачивать файлы
Вы не можете отвечать на сообщения
Вы не можете редактировать свои сообщения
Вы не можете удалять свои сообщения
Вы не можете голосовать в опросах
Вы не можете прикреплять файлы к сообщениям
Вы не можете скачивать файлы
Текущее время: 29-Ноя 21:31
Часовой пояс: UTC + 5
